
Telecom fraud is on a continuous rise and is one of the biggest sources of revenue loss amongst Telcos. As per a report from CFCA Fraud Loss Survey, Telecom Fraud Losses have increased by 28% between the years 2019 and 2021. The onset of the pandemic in 2020, further escalated telecommunications fraud and security threats.
According to a survey released by Mobileum Inc. (“Mobileum”), it has been found that 75% of operators polled were experiencing new or emerging incidents of fraud and 61% said network security threats increased significantly with the onset of the COVID-19 pandemic.
The report even provides data about the types of fraud loss in which IRSF and Traffic pumping incur to $6.69 billion and $4.54 billion respectively in 2021.
With these numbers, it becomes evident that to manage the pervasive threat of telco fraud, industry providers must have an effective fraud management approach that defends businesses and consumers.
What is Fraud Management in Telecom?
Frauds are not a new thing in the telecom industry – they have always been there. Technology is changing at a fast pace, and so are telecom fraud tactics. Fraudsters formulate new ways or simply tweak the existing methods to abuse telecommunications products and services. Their ultimate intention is to use services for free or illegally acquire money from CSPs or end users. High frequency, multiple layers of anonymity, and global nature help attackers to remain undetected.
An effective Telecom Fraud Detection Management process is a critical element in determining the success of a telecommunication company. Such a mechanism is important to detect and prevent fraudulent activities which can cause revenue losses. There are different types of telecommunication fraud that need to be addressed and handled by these mechanisms. Before we discuss this in detail, let us first take a look at the most common types of telecom fraud that one should know about.
Types of Telecom Fraud
Based on the target of the attackers, telecom frauds can be divided into two categories – Telcos and end users. Some of the major frauds that affect both carriers and end users are as mentioned below:
IRSF: International Revenue Share Fraud
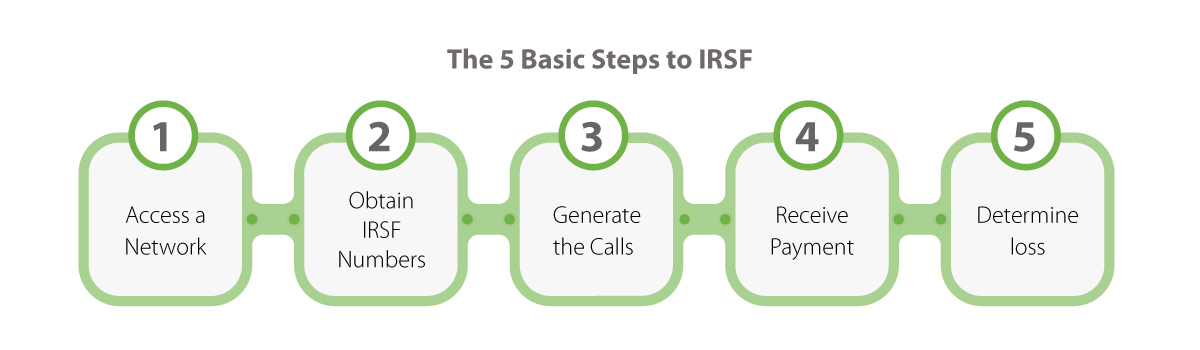
IRSF is one of the biggest fraud challenges for Telcos. In a report by CFCA, Revenue Share Fraud accounts for a $4 billion to $6.1 billion loss to the telecom industry. In this type of fraud attempt, the attackers take advantage of premium phone rates. Here’s how it happens:
- The attacker leases a premium phone number.
- The attacker then breaks into a business’s phone system and makes multiple calls to the premium rate number. Generally, these calls are made for a long duration to increase the phone bill.
- Huge phone bills are generated and paid by the business, 25% of which goes into the pockets of the attackers.
These calls are generally made outside a business’s working hours. Most of the time, companies do not realize that they have been attacked unless the time to pay the phone bill arrives.
Call Forwarding Fraud
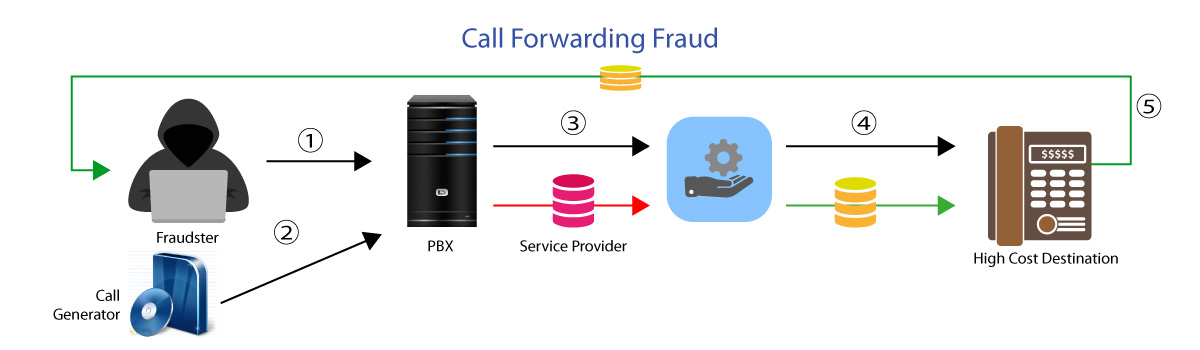
Call Forward fraud is a sophisticated form of telecommunication fraud. Attackers first hack access to the PBX system or IVR (Interactive Voice Response) of an enterprise. Then they configure call forwarding to a premium long-distance number. Once done, the attacker calls the phone number of the hacked PBX system which forwards the call to the premium number. Here the attacker earns profit from IRSF.
Wangiri Fraud
It is also known as ‘One Ring and Cut’ Fraud. Wangiri is a Japanese word that means one and cut. It’s a telephone scam that aims at striking curiosity among customers by calling from premium rate numbers. Each call is made to ring only once and is hung up. Thus, leaving a missed call on the recipient’s phone. The recipient often calls back without knowing that it’s a premium rate number controlled by fraudsters.
Interconnect Bypass Fraud
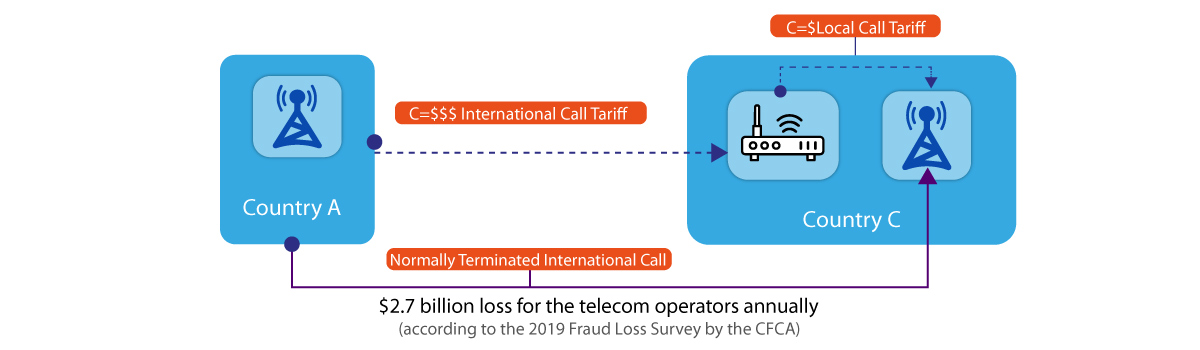 Also known as Toll Bypass Fraud or GSM Gateway Fraud, these types of frauds are executed by routing unauthorized traffic to a local operator via Sim Box or GSM Gateway. This is done so that the call terminates with the local operators and thus the expensive international interconnect gets replaced with an extremely low-cost routing channel. The bad actors thus earn the cost difference.
Also known as Toll Bypass Fraud or GSM Gateway Fraud, these types of frauds are executed by routing unauthorized traffic to a local operator via Sim Box or GSM Gateway. This is done so that the call terminates with the local operators and thus the expensive international interconnect gets replaced with an extremely low-cost routing channel. The bad actors thus earn the cost difference.
Wholesale SIP Trunking Fraud
In this type of fraud, the fraudsters make money by selling wholesale trunking services. The fraudsters use stolen credentials to terminate calls. Usually, a huge number of random calls are generated by fraudsters where destinations are not high cost but are not low cost either. This is how it is executed:
- The attacker steals the subscriber’s username and password
- Attacker’s softswitch registers with the service provider’s softswitch using stolen credentials
- A legitimate user places a call
- The attacker sends INVITE to the service provider’s softswitch
- Softswitch routes call to an international long-distance destination
Wholesale SIP trunking fraud is often difficult to detect. This is because the call patterns in these frauds look similar to normal subscriber usage.
Subscription Frauds
This type of fraud is executed by obtaining stolen identities (KYC documents) of customers from phishing attacks or purchasing from the dark web. Customer information is used to sign up for new telecom contracts and use their products and service but without the intention of paying them. It has been estimated that almost 40% of bad debts are actually subscription frauds.
How to Identify Fraud in Telecom?
Traditional Approaches to telecom fraud detection are based on the blacklisting of fraud phone numbers. But today attackers can simply bypass such detection by changing their phone numbers using VoIP. Some of the most common techniques for telecom fraud detection are:
- Collison Checks – Here the time period between two calls done by the same subscriber is checked for not colliding with a previously specified window.
- Velocity Checks – These types of frauds are detected by checking the GIS data to detect the distance between two locations and the delta time between the calls made by the same subscriber.
- New Subscriber Checks – In this type, false information is provided by the subscriber as he doesn’t intend to pay for the services used. Phonetic matches in the subscriber’s name are looked for in telecom fraud detection.
- Patten Checks – Here specific patterns in the user activities are looked upon. This is a powerful method and can be used to detect multiple types of fraud.
- Profile Checks – The calling pattern of the users is monitored and updated on their profile. Any unusual calling behavior may indicate fraud.
Best Practices for Telecom Fraud Prevention
We all know that prevention is better than cure. The same saying applies to the telecom fraud prevention scenario. Though attackers would always formulate new ways to penetrate into the systems, one should follow a proactive approach to fight telecom frauds. There are some golden countermeasures MNOs and MVNOs should always follow telecom fraud prevention. You can also read our post on SIP/VoIP Fraud Attacks
Here you go:
Password Protection

Always make sure that your software systems are protected with strong passwords, preferably a combination of alphanumeric characters. Also, it is important to change passwords periodically.
Monitoring PBX Systems
The most appropriate time for attackers to execute their attacks is after business hours, on weekends, and on holidays. Thus during these times, it becomes more important to monitor PBX systems for any unusual activities.
Clear the Clutter
Often we tend to keep old files in our systems that are of no use. But it is crucial to clear out all the junk files and folders from the system and deactivate unused features such as extensions.
Validate & Authenticate
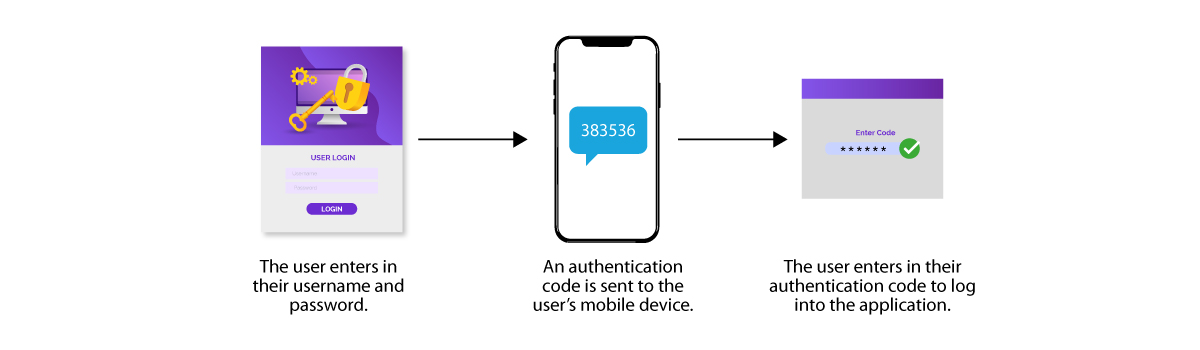
For a business, it is critical to cross-check and validate the details of its subscribers so as to filter out the fake ones. Also, applying 2 factor or multi-factor authentication is also an additional step towards ensuring security.
Keep an Eye on Expenditures
By doing a smart analysis of how much expenditure typically happens in a month, a business can keep a watch on any fraudulent activity. Many companies don’t do this, but tracking your expenses can help deter telecom scammers.
Use Security Software
Security software plays a crucial role in covering all grounds when it comes to security. Using intelligent security software like REVE Session Border Controller is a wise idea to keep telecom attacks at bay. REVE SBC is a Carrier-grade Cloud SBC that safeguards software switches from various types of attacks including DoS i.e. Denial of Service Attacks. It also includes intelligent firewall and state-of-the-art encryption techniques to protect a business from theft of service. Learn more about session border controller vendors.
Wish to learn more about Telecom Fraud Prevention? Just get in touch with our team to get the best security solutions.
Read Also
An Overview of Session Border Controller
How to Prevent Spoofed Robocalls with STIR/SHAKEN
Note- This post has been updated with the latest information on 21-04-2023.




























