
The modern networking landscape constantly evolves with innovative technologies like Network Function Virtualization (NFV) and its building blocks, Virtual Network Functions (VNFs). From the way they are designed and deployed to how they’re managed, these technologies are transforming every aspect of networks.
Through this blog, we will be discussing the intricacies of VNFs or Virtual Network Functions in detail. We will explore the role of VNFs in NFV frameworks through some practical examples. Also, we will understand how VNS, i.e., Visual Network Systems, enhance security within the NFV frameworks.
Sounds interesting? Let’s get started!
What is a Virtual Network Function or What is VNF?
As the term suggests, Virtual Network Functions are virtualized versions of traditional network functions that run over generic hardware instead of dedicated appliances. Before diving into the concept of VNFs, let me give you a background picture of traditional networks.
The traditional networking landscape typically relies on a rigid, hardware-centric approach. Such setups involve dedicated hardware appliances physically installed within data centers and connected via cables. These dedicated appliances are used for various network functions, such as firewalls, routers, and load balancers. Due to rigid architectures, traditional networks offer limited scalability.
Some of the major issues in traditional hardware-based networks are:
- Vendor Lock-in
Heavy reliance on dedicated hardware appliances from specific vendors for performing network functions makes it difficult to switch providers or integrate new functionality.
- Limited Agility and Flexibility
Slow adaptation to the rapidly evolving network demands and changing business needs.
- High Operational Costs
Management and maintenance of multiple physical devices lead to high upfront costs, maintenance expenses, and operational overhead.
- Scalability Challenges
Scaling traditional networks often meant buying more physical hardware, adding to expenses and efforts.
- Inefficient Resource Utilization
Hardware-based functions often aren’t fully utilized, leading to wasted resources.
The challenges and limitations posed by traditional networking environments led to the development and adoption of Virtual Network Functions or VNFs.
Imagine taking those bulky, dedicated hardware appliances from traditional networks and transforming them into software – that’s the essence of a Virtual Network Function. To accelerate new network service deployment while addressing all the above-mentioned challenges, service providers established ETSI and formed the ISG NFV working group in 2012.
In the following years, ETSI published papers on NFV use cases and defined NFV architecture in 2014. ETSI continues to innovate VNFs through projects, establishing standards for interoperability among networks from different providers.
In other words, VNFs represent a pivotal shift from traditional hardware-based network appliances to software-based solutions that run on standard hardware.
Understanding Network Functions
Just like the pieces of a jigsaw puzzle, network functions are the blocks that build the network. These functions have their own predefined rules and behaviors. Fundamentally, network functions are physical devices like a firewall box. However, advancements in technology have led to the emergence of virtual network functions that act just like physical devices but can be put on virtual machines. Virtual Network Functions eliminate the need to buy and install a physical device and are easy to deploy.
VNFs run inside virtual machines (VMs) or containers on common virtualization software such as VMWare or KVM. Multiple VNFs can share the same physical hardware, utilizing its resources efficiently. The management and coordination of VNFs happen within the NFV (Network Functions Virtualization) framework, ensuring smooth operation and scalability.
Key Benefits of Virtual Network Functions
A well-defined Virtual Network Function offers several key advantages. Let’s take a look:
Software-Defined
Unlike traditional network appliances, VNFs are software applications. They leverage virtualization technologies to decouple network functions from proprietary hardware.
On-Demand Scalability
VNFs are highly scalable, i.e., they allow organizations to dynamically add or remove additional instances of a VNF based on demand.
Flexible and Rapid Deployment
VNFs offer much more flexibility in terms of deployment, configuration, and customization. Be it an on-premise data center, public cloud, or hybrid infrastructure, VNFs can be deployed in various network environments. Moreover, VNFs can be provisioned much faster compared to traditional hardware-based appliances, thus allowing quicker deployment.
Cost-Effectiveness
VNFs eliminate the need for dedicated hardware, which reduces the huge upfront costs and maintenance expenses as well. Additionally, VNFs support ‘resource pooling’, i.e., generic hardware resources can be shared between multiple VNFs. This promotes optimum resource utilization, which further adds to cost efficiency.
Enhanced Security
VNFs provide enhanced security benefits as they offer faster updates, automatic threat response, and the ability to create custom security workflows.
How VNFs Work?
Understanding how VNFs work is important for grasping their role in the present-day networking landscape. Let’s break it down for you:
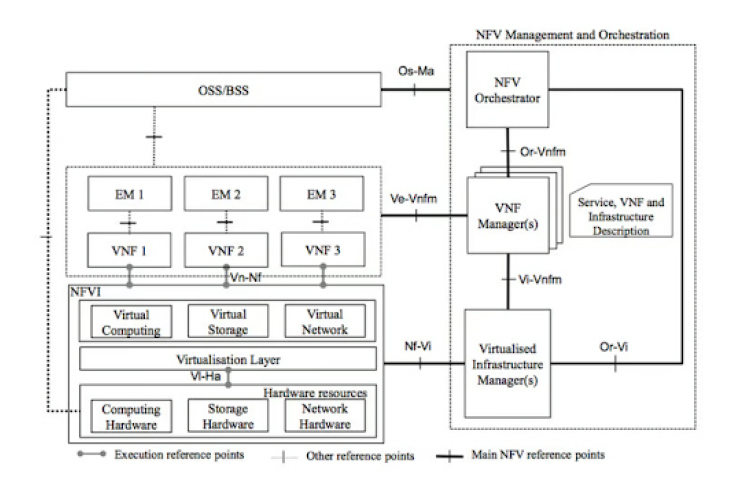
A VNF Manager or VNFM, considered the ‘operational backbone’ of the VNFs, contributes mainly to the operation of VNFs. It is a component within the NFV (Network Function Virtualization) architecture that interacts with NFV Orchestrator (NFVO) and Virtualized Infrastructure Manager (VIM) to orchestrate VNF deployments and their operations. From VNF instantiation configuration to scaling, monitoring, and termination, a VNF manager handles all these tasks to deliver reliable and efficient network services.
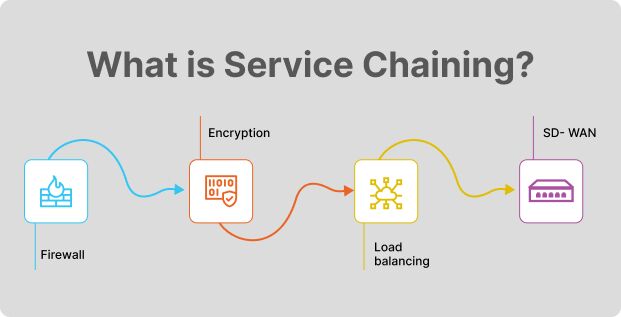
Virtual Network Functions facilitate service chaining, i.e., chaining multiple network functions together in sequence. Orchestrating the flow of different VNFs creates a service function path that ensures that data flows through the VNFs most efficiently.
Let’s consider an example for better understanding.
Suppose an organization deploys a VNF firewall within its virtualized network environment alongside various other VNFs, such as an IDS and a WAF. The firewall is configured according to the organization’s security policies and requirements, which include defining access control rules, logging and monitoring settings, and specifying blocked and allowed traffic. Additionally, service chaining rules are set up to define the sequence in which network traffic should be processed by the various VNFs.
As the network traffic moves, it encounters the VNF firewall. This firewall inspects the traffic, and based on its defined configurations, the VNF firewall enforces rules and filtering policies. After this, the traffic is forwarded to the IDS and then to the WAF. This ensures all incoming traffic is filtered for malicious activity before reaching your web applications.
Practical VNF Examples
Above, I have already explained one real-life VNF example in detail. Now, we will take a look at some other VNF examples that organizations within their virtualized network environments commonly deploy.
1. Virtual Load Balancer
This VNF performs the distribution of incoming traffic across multiple servers or applications. By doing so, a virtual load balancer ensures optimal utilization of resources, thus ensuring high performance and preventing the overloading of a single resource.
2. Virtual Router
This VNF provides routing functionalities to facilitate communication between different devices or network segments. Virtual routers enable organizations to create isolated network segments, manage traffic flow within cloud environments, and optimize routing paths. These VNFs are commonly integrated with SDN environments and VPNs as well.
3. Virtual Intrusion Detection and Prevention System (IDS/IPS)
This VNF monitors network traffic for signs of suspicious activity and security threats. These systems can generate alerts or take proactive actions to mitigate or prevent cyber-attacks, such as intrusions. Virtual IDS/IPS systems perform real-time inspection of network packets to detect anomalies and enforce security policies.
4. Virtual Session Border Controller (SBC)
A virtual SBC is used in Voice over IP (VoIP) and Unified Communications (UC) networks to manage and secure real-time communication sessions. It provides features such as call control, media routing, signaling, and security functions like encryption and authentication.
5. Virtual WAN Optimization Controller (WOC)
This VNF is used to optimize the performance and efficiency of the network. A virtual WAN WOC implements various acceleration techniques, including data compression, protocol optimization, and caching over WANs, resulting in reduced bandwidth utilization and a better user experience.
6. Network Address Translation (NAT) Services
This VNF provides a layer of security by assigning a single public IP address to multiple devices within a private network. This means that when these devices access the internet, the NAT router translates their private IP address to its public IP address and vice versa.
What is NFV?
You can think of Network Function Virtualization as a ‘grand stage’ where VNFs are the actors performing various network functions. However, two important things to remember here are that NFV is a virtualized stage that is not confined to physical hardware appliances. Also, VNFs are software-based actors that contribute to the overall functioning or success of NFV frameworks.
Insight: The roots of NFVs can be traced back to a white paper published in 2012, titled, “Network Functions Virtualization: An Introduction, Benefits, Enablers, Challenges & Call for Action”. Leading telecommunications providers, including AT&T, BT Group, Deutsche Telekom, Orange, Telecom Italia, and Verizon, contributed to outlining the concept of NFV through this whitepaper.
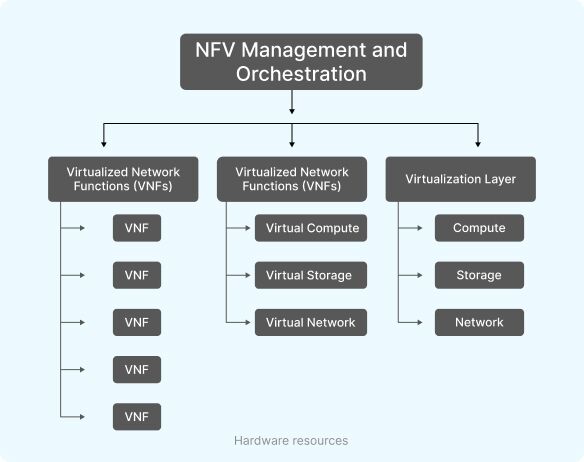
The NFV framework consists of several components, wherein three main components are:
1. Network Functions Virtualization Infrastructure (NFVI)
NFVI is the foundational hardware and software components that build the environment required for deploying and running VNFs within the NFV environment. It typically includes hardware platforms (servers, storage resources), virtualization software, cloud instances, and networking components.
Orchestration (MANO)
This is a broader term that refers to a set of functions and components within the NFV architecture that encompasses three main elements:
- NFV Orchestrator (NFVO): It is responsible for high-level orchestration and coordination of resources and services within the NFV environment. You can consider it as the conductor of the NFV orchestra that handles the entire lifecycle of VNFs, from deployment and configuration to scaling and updates.
- Virtualized Infrastructure Manager (VIM): It is responsible for managing and controlling the NFV infrastructure (NFVI) resources, including compute, storage, and networking resources.
- Virtual Network Function Manager (VNFM): It is responsible for managing the lifecycle of individual VNF instances.
3. NFV Infrastructure Manager (NFV IM)
This component is responsible for the management and control of the NFVI resources. From resource abstraction, pooling, and partitioning capabilities to support VNF deployments, the NFV IM performs multiple tasks.
VNF vs. NFV: Understanding the Difference
|
Feature |
Virtualized Network Function (VNF) |
Network Functions Virtualization (NFV) |
|
Definition |
Software implementation of a network function, replacing dedicated hardware. |
Architectural framework to decouple network functions from hardware, running them as software. |
|
Scope |
Specific virtualized network function (e.g., virtual firewall). |
Overall virtualization environment (infrastructure, management, VNFs). |
|
Nature |
Software entity (VM or container). |
Holistic approach and methodology. |
|
Components |
Software, configuration, data. |
NFVI, MANO, VNFs. |
|
Functionality |
Performs a specific network task. |
Enables virtualization of network node functions for agility and cost reduction. |
|
Deployment |
Deployed on virtualized resources within NFVI. |
Involves setting up infrastructure, MANO, and deploying VNFs. |
|
Management |
Managed by VNFM (within MANO) for lifecycle management. |
Managed by the overall NFV-MANO system. |
|
Hardware Dependency |
Independent of specific proprietary hardware (runs on COTS). |
Aims to reduce reliance on dedicated hardware. |
|
Examples |
Virtual Firewall, Virtual Router. |
OpenStack, ETSI NFV framework. |
|
Goal |
Virtualize individual functions for flexibility and efficiency. |
Transform network service delivery through virtualization. |
| Relationship | Building blocks within an NFV environment. |
Provides the platform and framework for VNFs. |
In the world of Network Function Virtualization, i.e., NFV, VNFs act as the building blocks of core components central to bringing the concept of NFV to life. While the two terms are interconnected and are used concurrently in modern networking, they represent different concepts. Let’s understand their key differences:
Definition
VNFs refer to specific network functions that are implemented as software and can run on virtualized infrastructure. NVS, on the other hand, is a broader concept that encompasses the virtualization of network functions and the orchestration of VNFs to create network services.
Scope
VNFs represent the specific software-based instances of network functions, whereas NFV is the entire framework for virtualizing network functions, including NFVI, NFV MANO, and the VNFs themselves.
Focus
VNFs focus on delivering specific network functionalities such as firewalling, switching, routing, etc. On the other hand, NFV focuses on the orchestration and management of network functions.
Level
VNFs are tangible and operate at the functional level, whereas NFV is the conceptual framework that operates at the architectural level.
Deployment
VNFs are deployed on top of NFVI (servers, virtual machines). On the other hand, NFV provides the platform for VNF deployment.
Management
VNFs can be managed by a VNF manager. Whereas NFVs are managed by NFVO, which includes VNF management.
Interoperability
VNF interoperability ensures that VNFs from various vendors work together seamlessly within an NFV environment. Whereas NFV standards and specifications promote interoperability between NFV components, enabling multi-vendor deployments and ecosystem integration.
Role of Visual Network Systems in Network Function Virtualization Security

Managing and securing a complex web of virtualized network functions within the context of NFV can be quite challenging. This is where the role of VNS, i.e., Visual Network Systems, comes into action.
What are Visual Network Systems?
VNS encompasses a range of software tools, platforms, and technologies that translate complex network infrastructure and traffic flow into clear and concise visual representations. VNS systems use graphical interfaces to provide visualizations of the NFV environment, including:
- Represents deployed VNFs such as firewalls, IDS/IPS, load balancers, etc., through icons or symbols.
- Depicts data flow, i.e., how data interacts with various VNFs, highlighting bottlenecks or security vulnerabilities.
- Visualizes connections between different VNFs, thus offering a clear picture of the overall workflow.
Importance of VNS in Network Visualization, Management, and VNF Security
Visual Network Systems play a pivotal role in enhancing network visualization, management, and security within Network Function Virtualization (NFV) deployments. Here’s why:
- Provides intuitive graphical representations that help network administrators gain useful insights and identify potential issues, facilitating better decision-making and troubleshooting.
- Fosters enhanced troubleshooting by offering data flow and connections between VNFs that help in identifying the root cause of the network problems faster.
- Aids in streamlined security management by highlighting security vulnerabilities by visualizing the specific security functions handled by different VNFs and the flow of data within the network.
- Enables simplified capacity planning as VNS systems showcase the resource utilization across VNFs, allowing administrators to ensure optimal resource allocation.
- VNS can help identify underutilized resources or potential bottlenecks within your VNF deployments, allowing for better resource allocation and optimized security posture.
- VNS can aid in demonstrating compliance with security regulations by providing a visual audit trail of network activity and security configurations.
Key Takeaway
In essence, a Virtual Network Function represents a significant advancement in network technology. VNFs are software applications that replicate hardware network appliances. NFV is the architectural framework for managing VNFs. Organizations must embrace the VNFs to establish a powerful, adaptable, and future-proof foundation for their network environments. Additionally, it is important to securely manage the complex web of VNFs for which Visual Network Systems act as powerful tools.
Frequently Asked Questions
What’s the difference between a VNF and a traditional network appliance?
A traditional appliance is a hardware device with integrated software, while a VNF is software decoupled from hardware, running on virtualized infrastructure.
Can traditional network appliances be replaced with VNFs?
In most cases, VNFs can replace hardware network appliances. However, when it comes to high-throughput or highly specialized applications, dedicated hardware may still be the preferred choice.
Can NFV exist without VNFs?
No. VNFs are essential to NFV; they are the functions that NFV is designed to virtualize and manage.
What industries benefit from VNFs and NFV?
Telecom, cloud service providers, enterprise IT, and data centers commonly benefit from these technologies.
Is NFV the same as SDN (Software Defined Networking)?
No, but they are complementary. NFV virtualizes network functions, while SDN separates the network control plane from the data plane.
Note: This post has been updated with the latest information on 08-04-2025.




























