What is Internet Protocol Security (IPsec)?
- July 31, 2025
- 14 Mins Read
- Listen

We’re all plugged in 24/7 – it’s a world where devices are constantly talking to each other. As this happens, data travels across vast, often public, IP networks, making them both powerful and vulnerable simultaneously. So, how do we ensure the safety of these networks? That’s where the concept of Internet Protocol Security, or IP network security, steps in.
We know that cybercriminals have become more sophisticated than ever, and IP network traffic continues to be a target. Whether it is a man-in-the-middle attack, data interception, or spoofing, organizations around the world face such dreadful threats daily. Industries dealing with sensitive user data, such as finance, healthcare, and telecoms, are always in danger of serious data loss, financial damage, and reputational harm.
IPsec plays a critical role in providing end-to-end protection for modern networks, ensuring confidentiality and tamperproofness of data as it moves across networks.
To fully understand its role, we need to take a closer look at IPsec- how it works, why it’s essential for securing modern networks, and how it integrates with tools like Session Border Controllers (SBCs) to deliver comprehensive network-layer protection.
What is IPsec?
IP stands for Internet Protocol Security, a suite of protocols designed to secure IP communications. This suite of protocols performs authentication and encryption of each IP packet within a data stream. While many security mechanisms operate at the application or transport layer, IPsec functions at the Layer 3, i.e., Network Layer of the OSI model. This is why IPsec can protect all types of IP traffic, regardless of the application or service generating it.
To precisely define the role of IPsec in cybersecurity, let’s take a look at the 3 major objectives it addresses:
Confidentiality
It restricts access to information from unauthorized parties using robust encryption algorithms. This means data stays encrypted and unreadable to outsiders
Integrity
It makes sure that data remains unaltered during transmission, typically enforced through detection mechanisms. This means that there are no edits or interference when data is sent.
Authentication
It checks and verifies the identities of the users or the system before exchanging data. This means one could be assured exactly who they are communicating with.
Protocols Used in IPsec
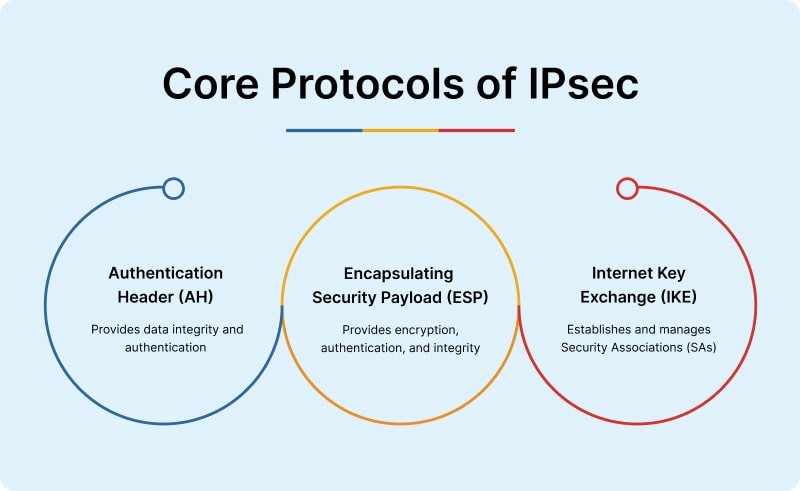
Now let’s get to the most interesting and useful part of IPsec – the suite of protocols that work together to provide layered security for IP communications.
Authentication Header or AH
As the name suggests, this protocol provides data integrity and authentication of the IP data packet. With this, it ensures that the data is not altered during the transmission. However, AH does not provide encryption, which means the payload in the data packet is still visible. The usefulness of AH comes in scenarios where encryption is not required but authenticity and integrity are crucial.
Encapsulating Security Payload or ESP
This protocol offers encryption, integrity, and authentication of the IP data packet. This is the reason why it is the most widely used component of IPsec. However, depending upon the configuration, ESP can be used with or without encryption. It is preferred in scenarios where there is a need to secure sensitive data over public networks.
Internet Key Exchange or IKE
The negotiation and management of security associations between endpoints is performed by this protocol. It does so by dynamically establishing shared encryption keys and managing key lifecycles.
How IPSec Works?
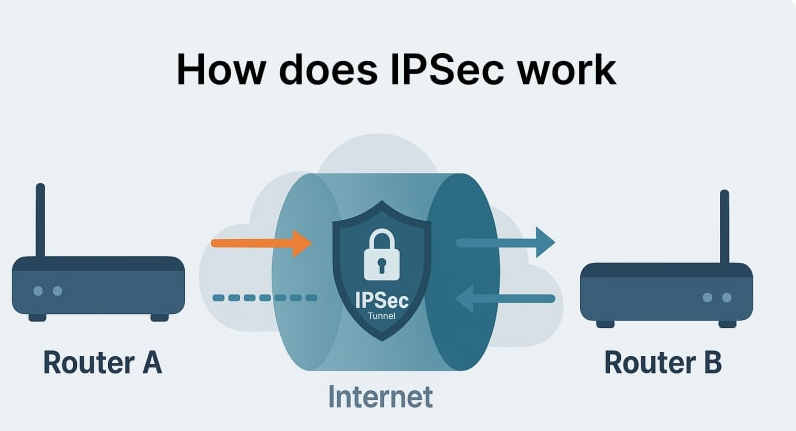
Establishing a Secure Relationship (Security Association)
Before any secure communication begins, IPsec needs to create a trusted channel between the two devices involved. This process is known as a Security Association (SA). To do this, IPsec uses the Internet Key Exchange (IKE) protocol, which handles the negotiation of security parameters. These include which encryption and hashing algorithms to use, how long the keys will last, and how keys will be exchanged safely.
Choosing the Right Mode of Operation
Once the secure channel is set up, IPsec needs to decide how the data will be protected during transmission. It does this using two modes: Transport Mode and Tunnel Mode.
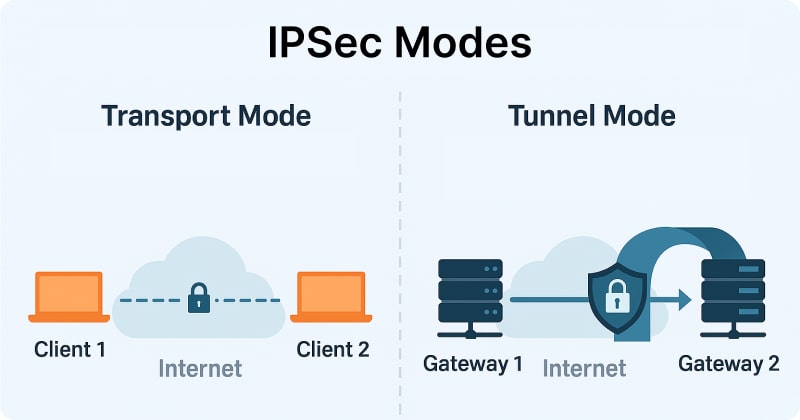
- In Transport Mode, only the payload (the actual content of the message) is encrypted, while the original IP header remains intact. This mode is ideal for end-to-end communication between two devices, such as a remote employee’s laptop accessing a corporate server.
- In contrast, Tunnel Mode encrypts the entire original IP packet, including the header, and then wraps it inside a new packet with a fresh IP header. This mode is most commonly used in VPNs or between gateways, like firewalls or routers, because it offers full-packet protection.
Applying Encryption and Authentication Protocols
With the mode selected, IPsec then applies specific protocols to secure the data: ESP (Encapsulating Security Payload) and/or AH (Authentication Header). ESP is more commonly used because it provides full confidentiality (encryption), integrity, and authentication. This means the message content is kept private, cannot be altered without detection, and comes from a verified source.
AH, on the other hand, offers only integrity and authentication, and it doesn’t encrypt the data, so it’s mainly useful when you want to verify trust but still allow visibility of the packet content. In most real-world use cases, such as sending OTPs or financial reports between secure servers, ESP is the preferred choice due to its robust protection.
Encrypting and Sending the Packet
Once everything is in place, the actual transmission process begins. The sender encrypts the IP packet according to the parameters defined in the Security Association. Depending on the chosen protocol and mode, the encrypted packet is either partially or fully sealed and then transmitted across the network. Upon reaching the destination, the receiver decrypts the packet, checks its integrity, and verifies its authenticity using the same agreed-upon parameters.
Only if the packet passes all these checks will it be accepted and passed on to the application (like a banking app or VoIP system). If anything seems off, like a tampered hash or unknown encryption, it’s discarded, ensuring that only secure and verified communication is allowed.
Key Refresh and Re-Negotiation
Security doesn’t stop after the initial exchange. Over time, the keys and parameters used to encrypt and authenticate messages can become vulnerable. To counter this, IPsec periodically refreshes the encryption keys and renegotiates Security Associations using IKE. This ensures that even if a key were to be compromised, the exposure is limited to a small window.
Benefits of Using IPsec in Cybersecurity
What exactly makes IPsec so valuable in cybersecurity? Let’s answer this commonly asked question in detail
End-to-End Encryption
The most powerful feature of IPsec is its ability to encrypt IP packets at the network layer, i.e., data is protected as it transits from one point to the other. So even if a hacker intercepts the traffic, they won’t be able to peek inside.
Strong Authentication & Data Integrity
Besides encryption, another strong feature of IPsec is its authentication and integrity capabilities. This means it verifies who the data is being sent to and also ensures that the data hasn’t been altered mid-transit.
Flexible Modes for Different Use Cases
As we already learnt at the beginning of this post that IPsec works in two modes – transport mode and tunnel mode. This means it’s not a one-size-fits-all tool and has the flexibility to adapt to the needs of the users.
Works with Both IPv4 and IPv6
And here’s the best part – IPsec is future-ready as well. By supporting both legacy and next-generation internet protocols, it ensures your security framework doesn’t fall behind.
Reduced Risk of Man-in-the-Middle (MITM) Attacks
IPsec makes MITM attacks almost impossible to happen by verifying both ends of the communication as well as encrypting the entire session. This means attackers cannot intercept, inject, or manipulate traffic in real-time.
Secure Remote Access
Remote teams can work from anywhere, even from untrusted networks like public WiFi in restaurants. However, IPsec ensures that hackers lurking on such public networks are not able to intercept.
Interoperability with Existing Systems
IPsec integrates seamlessly with a company’s existing tech stack because it is vendor-neutral and widely supported. Firewalls, routers, VPNs, and operating systems from different vendors typically support IPsec.
Meets Compliance & Regulatory Requirements
IPsec enables you to put a checkmark when it comes to meeting global security standards like HIPAA, PCI DSS, GDPR, and ISO/IEC 27001.
Common Use Cases of IPsec
To understand the relevance of IPsec across various industries, let’s move ahead to its key use cases, i.e., the variety of network security scenarios where it can be used
Virtual Private Networks (VPNs)
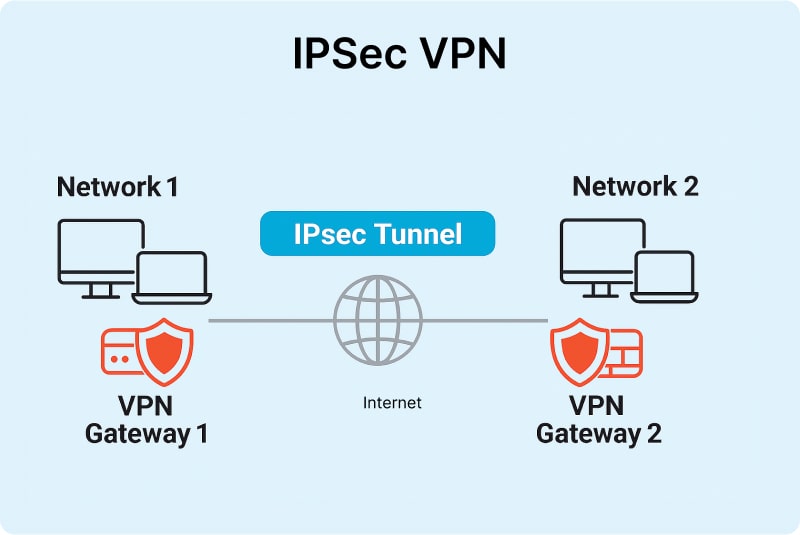
This is by far the most well-known use case for IPsec. VPNs are commonly used to enable secure communication over untrusted networks by creating encrypted tunnels. Consider a scenario where a remote employee uses a VPN client on his laptop to connect with his company’s internal network. The VPN application makes use of IPsec to encrypt the data being transmitted between the employee’s laptop and the company’s server. With this, it is ensured that the company’s confidential information, like documents, emails, and VoIP calls, remains tamper-proof.
Site-to-Site VPN for Branch Connectivity
Big organizations like MNCs have multiple branches at various geographical locations. IPsec helps such organizations in enabling secure communication between their branches over the internet without requiring private leased lines.
For example, a company with a head office in Delhi and branch offices in Bengaluru and Mumbai connects all its offices to the head office using site-to-site VPNs. IPsec tunnel mode is configured on the routers/firewalls at each office. When traffic from the Mumbai office LAN is destined for the Bengaluru office LAN, the Mumbai router encrypts the entire IP packet, encapsulates it in a new IP header, and sends it over the internet. The Bengaluru router receives this encrypted packet, decrypts it, and forwards it to the intended host on its local LAN.
Remote Access for Employees
Hybrid working is the new corporate norm, which means employees need secure access to corporate resources even when they work from unsecured networks. For instance, a remote IT consultant needs to debug a cloud server of the company. The company sets up an IPsec VPN to provide him with remote access to internal tools hosted on the company’s network, ensuring encryption and authentication of the connection.
Secure Communication Between Data Centers
Several enterprises across the globe run multiple data centers. This means they need secure communication for database backup, replication, and inter-service communication. For example, a SaaS company maintains two cloud regions in different geographical locations. They leverage IPsec tunnels to secure data replication, syncing, and failover traffic between the two locations.
Healthcare Data Protection
Healthcare facilities, including hospitals and clinics, often transmit sensitive Electronic Health Records (EHR) between locations, insurance providers, and labs. For instance, the clinic shares patient data with a diagnostic lab. Both parties use IPsec to secure communication and comply with medical data privacy standards such as HIPAA regulations.
Secure Financial Transactions
Secure communication is the foundation of the successful operation of any bank and financial institution. For instance, a bank makes use of IPsec to provide security while connecting its core transaction processing system with a government tax platform or an international payment gateway.
Government and Military Use
Security of data is an absolute necessity when it comes to defense, intelligence, and government sectors. They use IPsec to secure classified or confidential communication across agencies and international borders. This helps in ensuring that strategic data and commands remain confidential and unaltered.
IPSec and SBC: Comprehensive Security for Real-Time Communications
In VoIP and other real-time communications, Session Border Controllers (SBCs) play the role of the security personnel stationed at the entrance; they keep watch, sift through, and regulate all traffic entering and leaving your VoIP network. But what if this traffic must traverse insecure or public networks?
SBCs already provide application-layer security through protocols such as TLS for SIP signaling and SRTP for media stream encryption. These are great when both endpoints support them. But what happens if they don’t? Or when data is traversing an untrusted network where greater protection is required?
That’s where IPsec comes in as a strong supplement, offering network-layer security that protects everything below the app layer.
How SBCs Employ IPsec in Real-World Situations
Here are a few examples of real-world applications:
1. Secure SIP Trunking Over Public Internet
A telecommunication operator employs IPsec between the SBC of the telecommunication operator and an enterprise customer’s SBC to establish a secure tunnel across the public internet. This secure link prevents SIP signaling and RTP media traffic from being intercepted and manipulated.
Example: A bank employing a SIP trunk for customer support calls ensures that all voice information remains encrypted end-to-end through IPsec between the SBCs.
2. Hybrid Cloud Deployments
In hybrid configurations where some of the SBC infrastructure is on-premises and the remainder is cloud-hosted, IPsec enables safe connectivity between these environments. It establishes an encrypted tunnel that protects against packet sniffing, spoofing, or man-in-the-middle attacks as traffic travels between domains.
Example: A medical provider with an on-premises SBC securely connects to a cloud-hosted UCaaS platform through IPsec tunnels, protecting patient information.
3. Inter-SBC Communication in Carrier Networks
Multilevel carriers typically have several SBCs installed in different regions. When such SBCs must communicate with one another, for media relay, SIP routing, or call transfer, IPsec can encrypt that interconnection and make the communication secure.
Example: A VoIP carrier directs international calls through SBCs in London and Singapore, and employs IPsec to encrypt the voice and signaling traffic traversing international internet links.
Why IPsec Is Essential in Today’s SBC Strategy
- Public Network Exposure: If your SBC is interacting with third-party SBCs or carrier networks over the internet, IPsec is non-negotiable for secure communication.
- Zero Trust Architecture: Even within your own WAN or data centers, implementing IPsec aligns with zero-trust principles, assuming nothing is safe by default.
- Fallback When TLS/SRTP Aren’t Available: IPsec ensures encryption happens at the network layer, even in cases where application-layer encryption isn’t an option.
The Bigger Picture: Application + Network Layer Security
Imagine SBC + IPsec as a system of locking. TLS/SRTP handles at the application level, and IPsec takes care to wrap the entire packet at the network level
Combined, they offer end-to-end protection, shielding against attacks such as packet sniffing, SIP spoofing, and VoIP eavesdropping, vital for applications such as finance, healthcare, and government.
Conclusion
Securing IP-based traffic is no longer optional; it’s essential. That’s where IPsec comes in as a powerful tool in the cybersecurity arsenal. With its ability to encrypt, authenticate, and safeguard data at the network layer, IPsec ensures that sensitive communications remain protected from eavesdropping, tampering, and unauthorized access.
For telecom operators, aggregators, and enterprises using Session Border Controllers (SBCs), IPsec adds an extra layer of defense. It works behind the scenes to secure SIP signaling, media streams, and inter-SBC connections, especially vital when dealing with public or hybrid networks.
Whether you’re managing VoIP infrastructure, deploying secure VPNs, or ensuring compliance in regulated sectors like finance or healthcare, IPsec plays a foundational role in building trust over the internet. Implementing it wisely, especially alongside technologies like SBCs, enables businesses to strike the perfect balance between performance, scalability, and robust security. To get expert consultation, register here.
Frequently Asked Questions
What happens if an IPsec tunnel drops during a call?
The VoIP call may be interrupted unless there’s a failover mechanism or secondary link configured.
Does IPsec affect call quality?
IPsec introduces minimal latency and overhead, but modern hardware and optimized configurations keep the impact on voice quality negligible.
Is IPsec compliant with telecom regulations?
Yes. IPsec supports compliance with standards like GDPR, HIPAA, and PCI-DSS when used properly with SBCs.
What industries benefit most from SBC + IPsec?
Finance, healthcare, government, and contact centers that handle sensitive data and large volumes of VoIP calls.
Does IPsec provide end-to-end encryption?
Yes, when deployed correctly in transport or tunnel mode, IPsec offers full encryption from one endpoint to another.
Can IPsec be used for SIP trunking security?
Yes. IPsec is widely used to protect SIP trunks, especially when connecting an enterprise SBC to a carrier’s network over the Internet.

























